1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
| #include <iostream>
#include <Windows.h>
using namespace std;
#define HIBYTE(x) (*((byte*)&(x)+1))
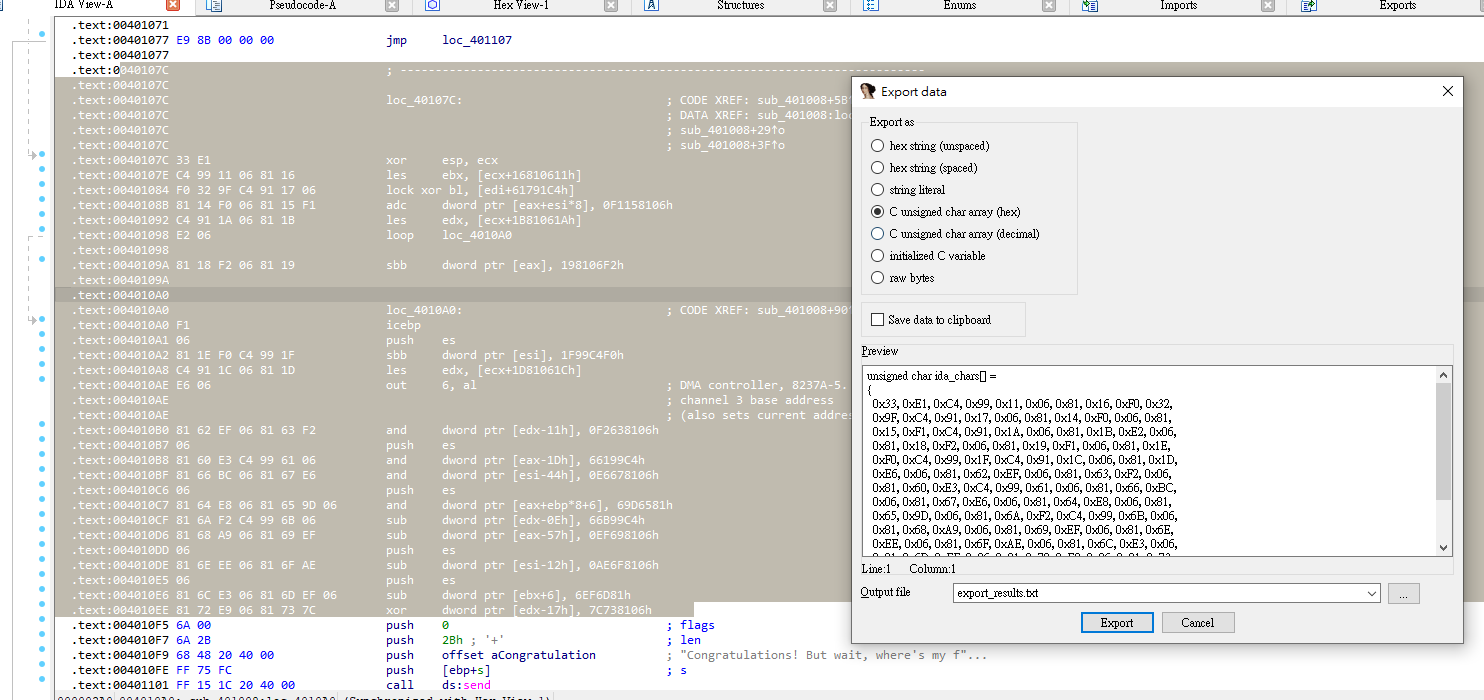
unsigned char arr[] =
{
0x33, 0xE1, 0xC4, 0x99, 0x11, 0x06, 0x81, 0x16, 0xF0, 0x32,
0x9F, 0xC4, 0x91, 0x17, 0x06, 0x81, 0x14, 0xF0, 0x06, 0x81,
0x15, 0xF1, 0xC4, 0x91, 0x1A, 0x06, 0x81, 0x1B, 0xE2, 0x06,
0x81, 0x18, 0xF2, 0x06, 0x81, 0x19, 0xF1, 0x06, 0x81, 0x1E,
0xF0, 0xC4, 0x99, 0x1F, 0xC4, 0x91, 0x1C, 0x06, 0x81, 0x1D,
0xE6, 0x06, 0x81, 0x62, 0xEF, 0x06, 0x81, 0x63, 0xF2, 0x06,
0x81, 0x60, 0xE3, 0xC4, 0x99, 0x61, 0x06, 0x81, 0x66, 0xBC,
0x06, 0x81, 0x67, 0xE6, 0x06, 0x81, 0x64, 0xE8, 0x06, 0x81,
0x65, 0x9D, 0x06, 0x81, 0x6A, 0xF2, 0xC4, 0x99, 0x6B, 0x06,
0x81, 0x68, 0xA9, 0x06, 0x81, 0x69, 0xEF, 0x06, 0x81, 0x6E,
0xEE, 0x06, 0x81, 0x6F, 0xAE, 0x06, 0x81, 0x6C, 0xE3, 0x06,
0x81, 0x6D, 0xEF, 0x06, 0x81, 0x72, 0xE9, 0x06, 0x81, 0x73,
0x7C
};
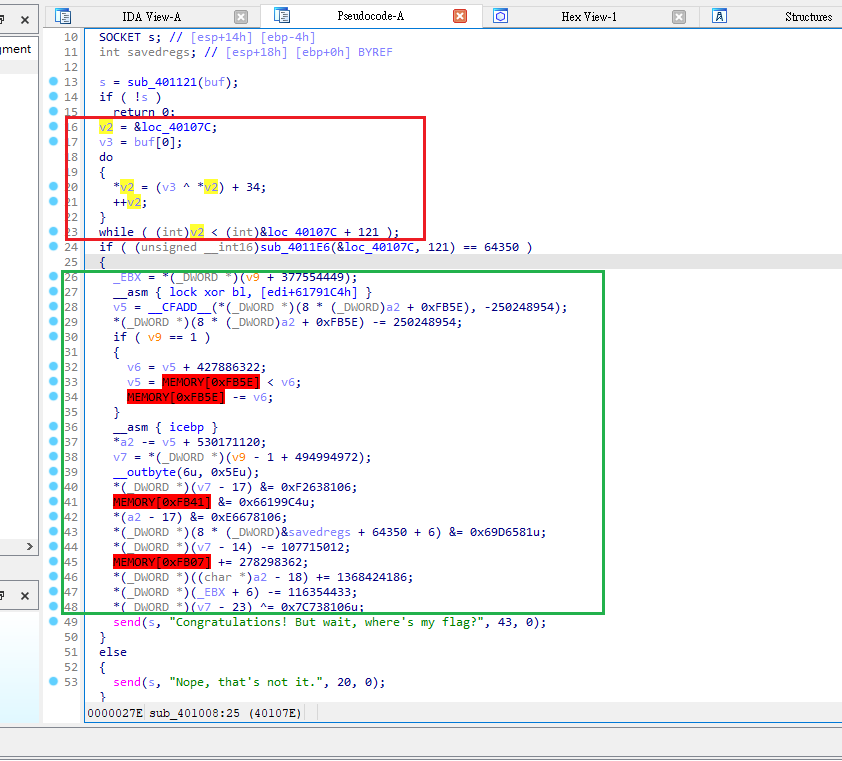
__int16 __cdecl sub_4011E6(unsigned __int8* a1, unsigned int a2)
{
unsigned int v2;
unsigned __int16 v3;
unsigned __int16 v5;
int v6;
unsigned __int16 i;
v2 = a2;
v3 = 255;
for (i = 255; v2; v3 = HIBYTE(v3) + (unsigned __int8)v3)
{
v5 = i;
v6 = v2;
if (v2 > 0x14)
v6 = 20;
v2 -= v6;
do
{
v5 += *a1;
v3 += v5;
++a1;
--v6;
} while (v6);
i = HIBYTE(v5) + (unsigned __int8)v5;
}
return (HIBYTE(i) + (unsigned __int8)i) | ((v3 << 8) + (v3 & 0xFF00));
}
int main() {
for (int i = 0; i < 256; i++) {
unsigned char v2[121];
memcpy(v2,arr,0x79);
for (int j = 0; j < 0x79; j++) {
v2[j] = (i ^ v2[j]) + 0x22;
}
if ((unsigned __int16)sub_4011E6((unsigned __int8*)&v2, 0x79u) == 0xFB5E) {
cout << i << endl;
break;
}
}
}
|

/image3.png)
/image.png)