【DASCTF八月挑战赛】apkrev
好久沒更新blog了,也好久沒有玩CTF了,來水一篇好了^^
分析
易知具體邏輯在so層
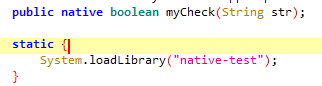
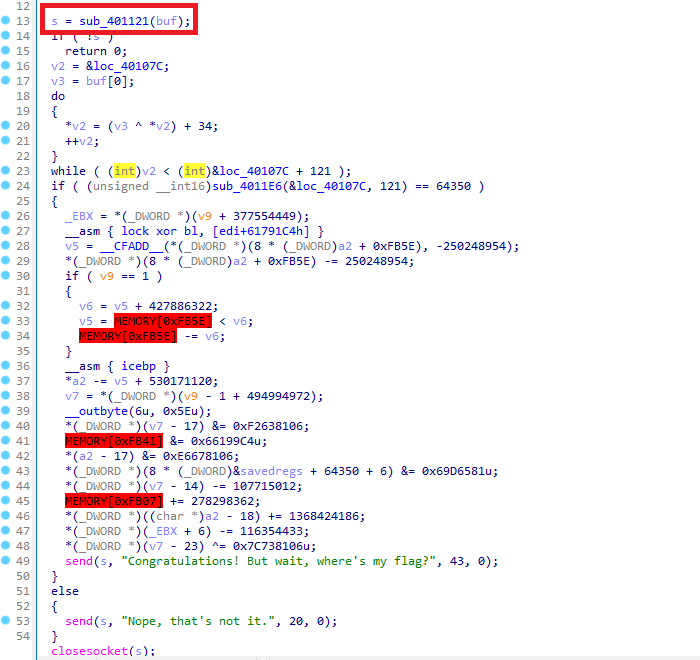
- 分析後發現如下位置,最關鍵的就是那個與
input異或的v13 - 並且這個
v13高機率是固定的
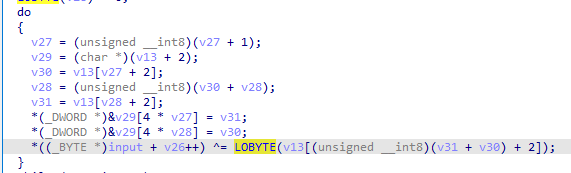
異或完之後就與enc對比,全對才返回true
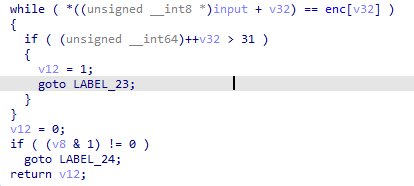
解法
- 由上述分析可知那個
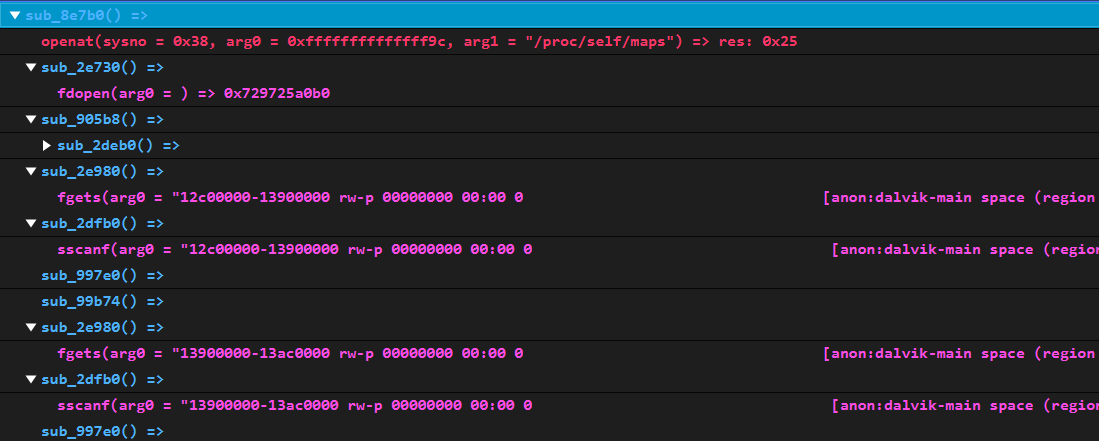
v13異或數組是最關鍵的 - 我選擇使用指令trace的方式來獲取這個
v13,用的是這個項目來生成trace日志 - 生成的trace日志裡有以下這段,
0xf3,0x3f...就是v13數組( 這其實少了第一個元素0xbb)
1 | instruction 0x776a2c1430 0x776a2c13f8 4 ldr w12, [x12, w14, uxtw #2] |
解密腳本:
1 |
|
本部落格所有文章除特別聲明外,均採用 CC BY-NC-SA 4.0 許可協議。轉載請註明來自 NgIokWeng's Blog!
評論

/image3.png)
/image.png)